Recent News
System on Chip Hardware & Software Cybersecurity
Welcome to the CAP Center
The Leader in Hardware and Software Cybersecurity
Our mission is to provide the electronics industry and intelligence community with knowledge, methodology, solutions, and skilled cybersecurity engineers to help prevent penetration and manipulation of our nation’s cyber-physical infrastructures. We use noninvasive hardware and software reverse engineering techniques to assess physical layer cybersecurity vulnerabilities in embedded systems, specifically IoT devices. We also develop countermeasures to secure them against sensitive data extraction, disruption, diversion, and obfuscation.
We specialize in providing information on system on chip hardware and software cybersecurity. System on a chip hardware allows for the creation of smaller and more efficient devices, driving innovation in the creation of netbooks, laptops, smartphones, and IoT devices. By partnering with CAP, you can expect to understand the best system-on-chip hardware and hardware cybersecurity solutions on the market today. Our partners enjoy the very best in hardware security practices.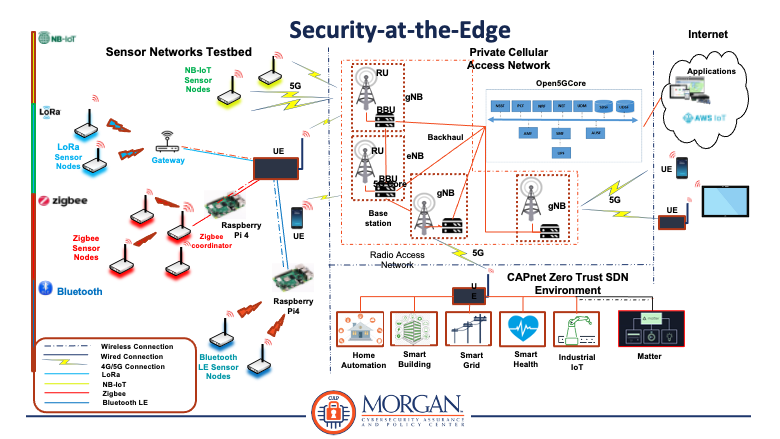
RESEARCH AREAS
- Hardware Security
- Side Channel Analysis (SCA)
- Simple Power Analysis (SPA)
- Differential Power Analysis (DPA)
- Correlation Power Analysis (CPA)
- Differential Electromagnetic Analysis (DEMA)
- Fault Injection (FI)
- System on Chip Design
- Security-at-the-Edge
- Secure System-on-Chip (SoC) Design
(e.g., Intel 16 nm CMOS Technology) - Hardware/Software Reverse Engineering
- Countermeasure Assessment and Development
- Wireless Interface/Protocol Vulnerability Assessment
(e.g., 5G, Matter, etc.) - Trustworthy AI